Hackers send you an email with a malicious link and try to trick you into clicking it. Once hackers gain control of a phone number they can then access their online profiles on Facebook Twitter.
 How Can I Tell If My Phone Has Been Hacked Nortonlifelock
How Can I Tell If My Phone Has Been Hacked Nortonlifelock
If you fear being hacked in a public space turning off your phone can block a hackers ability to hack you this is an effective preventative method.

Can hackers access your phone. Hackers can gain access to your phone in several ways but they almost all require action on your part. Hackers transfer your phone number to their device and gain access to your account. Vulnerabilities exist that let a hacker see your texts tap your calls and see your location.
For example if you have been hacked by spy apps you might be satisfied with just removing the spy app. The serious cause for concern here is that hackers can actually lock down every information in your phone till the ransom is paid. Its common for hackers to send fake text messages to their targets in order to gain username and password.
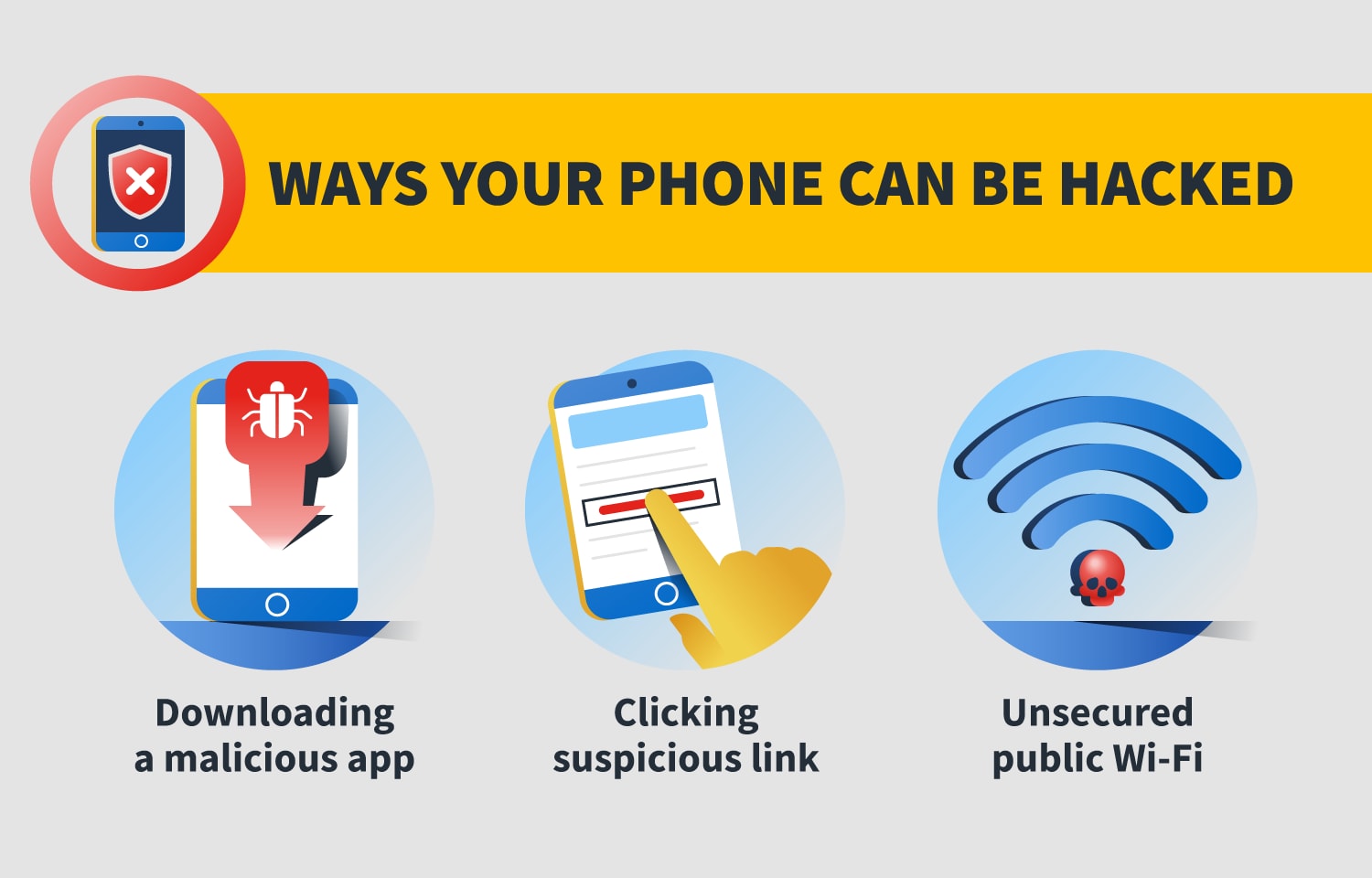
Such emails or texts may look very real and sometimes it may be complicated to distinguish between a malicious site and a legitimate one. And avoid clicking on anything that pops up. Attackers send bait text messages in the form of trustworthy sources.
Websites are another possible place where you can accidentally pick up software that allows hackers to access your iPhone. They can also use your number in. When a hacker gets into your phone they will try to steal access to your valuable accounts.
No someone cant hack your phone just by calling you. Yes someone can hack your phone by texting you. How they have managed to hack you can influence your response.
So again it would be wise to enable the Touch ID security feature or a complicated password to thwart access into your banking app. Therefore if someone hacks your phone they would have access to the following information. Email addresses and phone numbers from your.
Even your smartphone could be infected with a ransomware and hackers can hold your phone ransom till you shell out some money. For example your phone can be hacked if you have. Your credit card has just.
Skilled hackers can take over a hacked smartphone and do everything from making overseas phone calls sending texts and using your phones browser to shop on the Internet. With the right malware a hacker can access your phone and scan your pocket for the RFID enabled credit card. Your phone number is an easy-to-find key that can be used by hackers and scammers to unlocking your personal data.
How hackers can use your number to get access to your personal information. Check your social media and email for password reset prompts unusual login locations or new account signup verifications. Such methods are called smishing or phishing.
You notice unfamiliar calls or texts in your logs. That said there are a few ways a hacker can use your phone number to help get extra access as part of a larger attack. If you can only visit well-known websites.
To turn off your iPhone hold down the power button on the upper right-hand side of your phone. They can then take this data and use a magnetizing device to upload the stolen credit card data onto a blank card. Hackers can access your mobile and laptop cameras and record you cover them up now.
One of the easiest ways for hackers to invade your phone and access your information is through your email inbox. In a more likely scenario if a hacker manages to take control of your phone they could access your banking app and initiate a cashless ATM transaction. Phishing for personal data.
These attacks allow hackers to access your phone through texts. Through unauthorized use of your phoneremotely. However that doesnt mean your phone cant be hacked via its cellular connection.
Why havent these vulnerabilities been patched. Phishing emails or texts. Hackers may be tapping your phone with an SMS trojan.
Hackers can get the codes by bribing phone company employees for instance. However ransomware is not just a corporate menace. Phishing scams are designed to.
If you have read through my articles above youll know that there are several ways hackers can gain access to your phone. Since theyre not paying your smartphone bill they dont care about exceeding your data limits. It is fairly easy for hackers to connect to your phone using WIFI or Bluetooth so turn them off when not needed because there is no warning when a hacker attacks you.
Downloaded a malicious app.